Network Connectivity
Agent Communications
The CloudCasa agent connects out to the CloudCasa service at the endpoint agent.cloudcasa.io:443, and all control traffic travels on this connection.
If your cluster is running in a private network and has no access to the public Internet, it will not be able to connect to the above endpoint. However, CloudCasa supports connectivity via AWS PrivateLink. So if your cluster is running in an AWS VPC, you will be able to use AWS PrivateLink to set up a private connection to the CloudCasa service. If you are interested in making use of this feature, contact CloudCasa support.
If your cluster is running in other cloud providers such as Azure or GCP, it may still be possible to set up a private connection. Contact CloudCasa support for further details.
Note PrivateLink connections to CloudCasa are only available with paid service plans.
The following topology diagram illustrates the principal services and network connections used by the CloudCasa agent. Firewalls must be configured to allow the necessary connections.
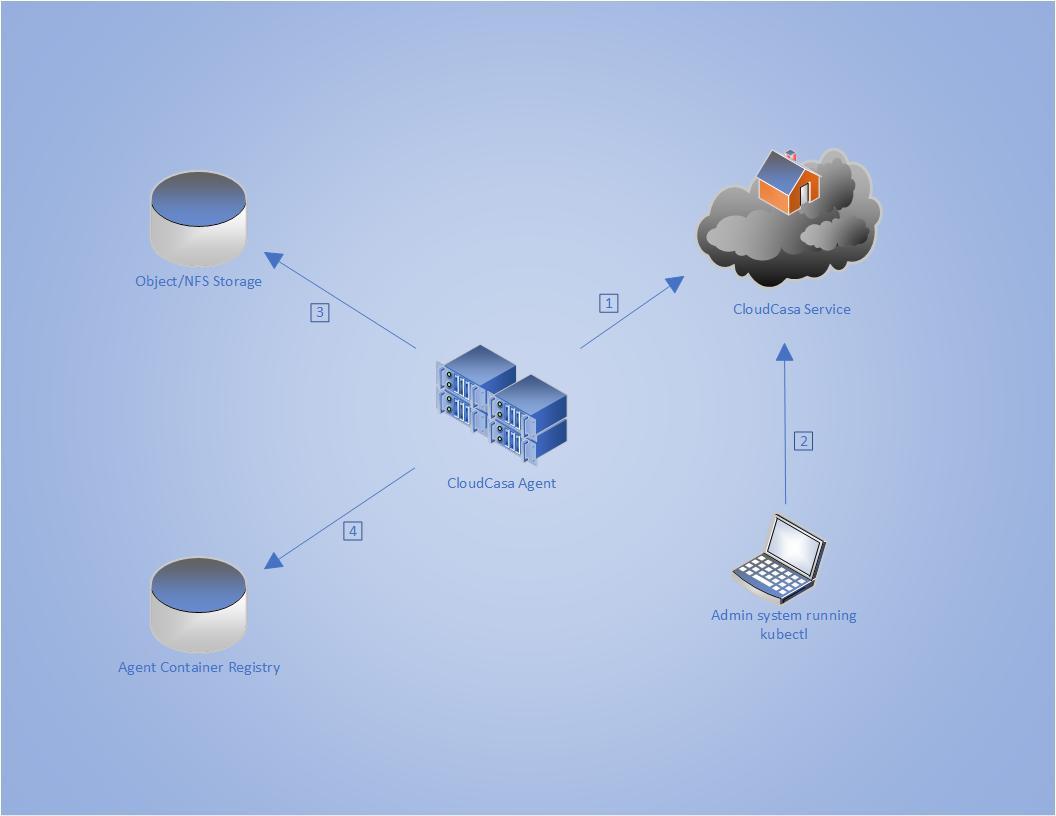
- ① agent.cloudcasa.io:443
The agent initiates and maintains a control connection to CloudCasa at this address.
- ② api.cloudcasa.io:443
This is used only to fetch the agent manifest YAML file for use by
kubectlwhen initially installing the agent. Alternate installation methods are available. Contact CloudCasa Support for more information.- ③ Storage
For backups and restores, the agent must be able to open a connection to whatever object or NFS storage is configured to be used for backup storage. This can be local or remote.
- ④ Container Registry
The backup client cluster needs to connect to the configured container registry on TCP 443 to load the CloudCasa agent containers.
Web UI Communications
In order to make use of the CloudCasa web UI, the user’s browser must be able to communicate with several public Internet endpoints in the cloudcasa.io domain.
home.cloudcasa.io:443auth.cloudcasa.io:443api.cloudcasa.io:443grpcapi.cloudcasa.io:443
In highly restricted environments, outbound connections to these endpoints may need to be explicitly allowed.